On Friday evening, Microsoft released patches for Windows XP, Server 2003, and Windows 8, after those systems were infected with Ransomware on Friday.

WannaCrypt, a variant of WannaCry ransomware, used previously leaked NSA tools to exploit vulnerabilities in the Windows platform.
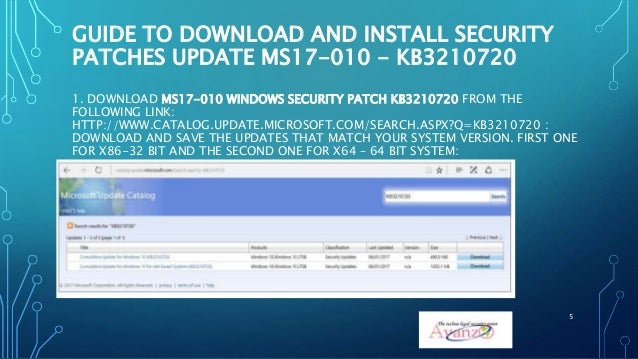
May 13, 2017 Download updates for Windows XP, Windows 8, or Windows Server 2003: All, Now that Microsoft have. The script should work in either Powershell v2 or v4 and contains all the Hot Fix numbers as of 5/16/2017 that contain the MS17-010 patch (each rollup update will replace the existing HotFix with a new KB number).
The WannaCry attacks on Friday reached 125,000 systems worldwide, impacting the National Health Service in the UK, as well as shipping giant FedEx. The ransomware infection spread quickly Friday afternoon, as the attackers leveraged code stolen from the NSA (EternalBlue / DoublePulsar) to target Server Message Block (SMB) protocol in Windows.
Microsoft patched the vulnerability in March, but only for current platforms, or for those with special support contracts. For the most part, users on Windows XP, Windows 8, and Server 2003 were not provided a fix.
However, after Friday's attack, Microsoft changed their stance on EOL (end-of-life) patching and provided fixes for everyone.
'Today many of our customers around the world and the critical systems they depend on were victims of malicious “WannaCrypt” software. Seeing businesses and individuals affected by cyberattacks, such as the ones reported today, was painful. Microsoft worked throughout the day to ensure we understood the attack and were taking all possible actions to protect our customers,' Microsoft explained.
'Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download. This decision was made based on an assessment of this situation, with the principle of protecting our customer ecosystem overall, firmly in mind.'
Redmond released patches for Windows Server 2003 (SP2 x64 / x86); Windows XP (SP2 x64, SP3 x86); Windows XP Embedded (SP3, x86); as well as the 32-bit and 64-bit versions of Windows 8.
For details on MS17-010, the patch that addresses the SMB vulnerability, the advisory can be found here.